
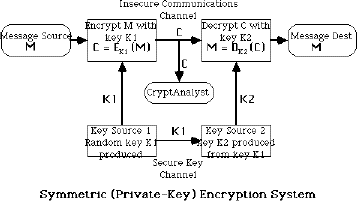
Encryption C = E_(K)(P)
Decryption P = E_(K)^(-1)(C)
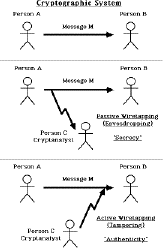
E_(K) is chosen from a family of transformations known as a cryptographic system.
The parameter that selects the individual transformation is called the key K, selected from a keyspace K
More formally a cryptographic system is a single parameter family of invertible transformations
E_(K) ; K in K : P -> C
with the inverse algorithm E_(K)^(-1) ; K in K : C -> P
such that the inverse is unique
Usually assume the cryptographic system is public, and only the key is secret information
L FDPH L VDZ L FRQTXHUHG I CAME I SAW I CONQUERED
 ie mapping is
ie mapping is
ABCDEFGHIJKLMNOPQRSTUVWXYZ DEFGHIJKLMNOPQRSTUVWXYZABC
Decryption D_(k) : i -> i - k mod 26
GDUCUGQFRMPCNJYACJCRRCPQ HEVDVHRGSNQDOKZBDKDSSDQR Plain - IFWEWISHTOREPLACELETTERS JGXFXJTIUPSFQMBDFMFUUFST KHYGYKUJVQTGRNCEGNGVVGTU Cipher - LIZHZLVKWRUHSODFHOHWWHUV MJAIAMWLXSVITPEGIPIXXIVW
Single Letter Double Letter Triple Letter E TH THE T HE AND R IN TIO N ER ATI I RE FOR O ON THA A AN TER S EN RES
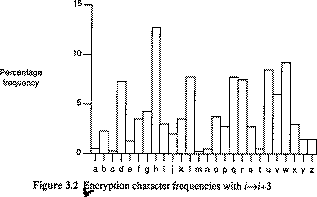
nb a must not divide 26 (ie gcd(a,26) = 1)
otherwise cipher is not reversible eg a=2
and a=0, b=1, c=2 ... , y=24, z=25
Example - Sinkov pp 34-35
Plain: ABCDEFGHIJKLMNOPQRSTUVWXYZ Cipher: DKVQFIBJWPESCXHTMYAUOLRGZN Plaintext: IFWEWISHTOREPLACELETTERS Ciphertext: WIRFRWAJUHYFTSDVFSFUUFYA
2) can solve the problem piece by piece
(ie can get key nearly right, and nearly get message)
(near enough MUST NOT be good enough!)
Cryptanalysis
Example Seberry p66
STARW BCDEF GHIJK LMNOP QUVXY Z Plain: ABCDEFGHIJKLMNOPQRSTUVWXYZ Cipher: SBGLQZTCHMUADINVREJOXWFKPY Plaintext: I KNOW ONLY THAT I KNOW NOTHING Ciphertext: H UINF NIAP OCSO H UINF INOCHIT
Plaintext THISPROCESSCANALSOBEEXPRESSED Keyword CIPHERCIPHERCIPHERCIPHERCIPHE Plaintext VPXZTIQKTZWTCVPSWFDMTETIGAHLH

ABCDEFGHIJKLMNOPQRSTUVWXYZ A ABCDEFGHIJKLMNOPQRSTUVWXYZ B BCDEFGHIJKLMNOPQRSTUVWXYZA C CDEFGHIJKLMNOPQRSTUVWXYZAB D DEFGHIJKLMNOPQRSTUVWXYZABC E EFGHIJKLMNOPQRSTUVWXYZABCD F FGHIJKLMNOPQRSTUVWXYZABCDE G GHIJKLMNOPQRSTUVWXYZABCDEF H HIJKLMNOPQRSTUVWXYZABCDEFG I IJKLMNOPQRSTUVWXYZABCDEFGH J JKLMNOPQRSTUVWXYZABCDEFGHI K KLMNOPQRSTUVWXYZABCDEFGHIJ L LMNOPQRSTUVWXYZABCDEFGHIJK M MNOPQRSTUVWXYZABCDEFGHIJKL N NOPQRSTUVWXYZABCDEFGHIJKLM O OPQRSTUVWXYZABCDEFGHIJKLMN P PQRSTUVWXYZABCDEFGHIJKLMNO Q QRSTUVWXYZABCDEFGHIJKLMNOP R RSTUVWXYZABCDEFGHIJKLMNOPQ S STUVWXYZABCDEFGHIJKLMNOPQR T TUVWXYZABCDEFGHIJKLMNOPQRS U UVWXYZABCDEFGHIJKLMNOPQRST V VWXYZABCDEFGHIJKLMNOPQRSTU W WXYZABCDEFGHIJKLMNOPQRSTUV X XYZABCDEFGHIJKLMNOPQRSTUVW Y YZABCDEFGHIJKLMNOPQRSTUVWX Z ZABCDEFGHIJKLMNOPQRSTUVWXY
then f_(i) (a) = a + k_(i) (mod n)
then f_(i) (a) = (k_(i) - a) (mod n)
and its inverse is
f_(i) ^(-1)(a) = (k_(i) - c) (mod n)
Example - Seberry p71
Key = d Plain: ABCDEFGHIJKLMNOPQRSTUVWXYZ Cipher: DCBAZYXWVUTSRQPONMLKJIHGFE
then f_(i) (a) = a - k_(i) (mod n)
where H(K) is entropy (amount of info) of the key,
and is D the rate of the language used (eg 3.2)
hence only need 2 letters to break
hence only need 27 or 28 letters to break
hence need 1.5 times the number of separate substitutions used letters to break the cipher
Example - Seberry p71
Plaintext: TOBEORNOTTOBE Key: NOWNOWNOWNOWN Ciphertext: GCXRCNACPGCXR
Since repeats are 9 chars apart, guess period is 3 or 9.
see Seberry Table 3.2 p72 and Table 3.3 p74
d IC 1 0.0660 2 0.0520 3 0.0473 4 0.0450 5 0.0436 6 0.0427 7 0.0420 8 0.0415 9 0.0411 10 0.0408 11 0.0405 12 0.0403 13 0.0402 14 0.0400 15 0.0399 ... ... Inf 0.0380
Table 3.3 - Period and IC for English
MR = Isu(i=o,n-1,(p_(i) - F(1,n))^(2))where p_(i) is probability an arbitrary character in ciphertext is the ith character a_(i) in the alphabet
Isu(i=o,n-1,p_(i)) = 1
MR = Isu(i=o,n-1,p_(i)^(2)) - 0.038or
MR + 0.038 = Isu(i=o,n-1,p_(i)^(2))is prob two arbitrary letters in ciphertext are the same
Bbc[(S(N,2)) = F(1,2) N (N-1)
F(F_(i)(F_(i)-1),2) and Isu(i=o,n-1,F_(i)) = 1
IC = Isu(i=o,n-1,F(F_(i)(F_(i)-1),N(N-1)))and use the IC estimate in
MR + 0.038 = IC
0.038 < IC < 0.066
Exp(IC) = F(1,d) F(N-d,N-1)(0.066) + Bbc[(S(d-1,d))F(N,N-1)(0.038)and we can use these values to estimate d from the ciphertext
Example program to compute IC - Seberry Fig3.4 p74
Example - Seberry pp73-77
Command Meaning
? this message.
! execute a shell command.
f [<seqlen> [n]] print [the n most] frequent strings of length seqlen.
g [<d> <p>] print the frequency distribution graph of letters.
i [<p>] calculate the index of coincidence of the text.
l [<b> <B>] list only the modified string. [b=blklength, B=blks/line]
p print current code.
q exit.
s <ch1> <ch2> substitute ch2 for ch1.
S [-] -[gvbB] {keys} Perform the substitution specified by the key.
T [-] <perm>|key Transpose text by perm or keyword. e.g. T 4,5,2,3,1
t <n> [/regexp] look for transpositions of period n; [print only /regexp].
B [-] <perm>|key apply the specifed rectangular encryption to the text.
b <n> [/regexp] look for block decryptions of size n; [print only
/regexp].
u undo previous modification.
z reset the code to its initial state.
r <file> enter code from file.
w <file> write code to file.
e edit code.
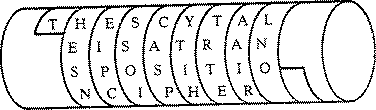
For information on lots of simple substitution and permutation ciphers see:
Plain: I CAME I SAW I CONQUERED Cipher: DEREU QNOCI WASIE MACI
Plain: I A E S W C N U R D
C M I A I O Q E E
Cipher: IAESW CNURD CMIAI OQEE
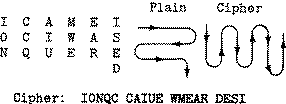
Plain: THESIMPLESTPOSSIBLETRANSPOSITIONSXX
Key (R): 2 5 4 1 3
Key (W): 4 1 5 3 2
T H E S I S T I E H
M P L E S E M S L P
T P O S S S T S O P
I B L E T E I T L B
R A N S P S R P N A
O S I T I T O I I S
O N S X X X O X S N
Cipher: STIEH EMSLP STSOP EITLB SRPNA TOIIS XOXSN
Example - Davies p26 Fig 2.14
Plain: ACONVENIENTWAYTOEXPRESSTHEPERMUTATION
Key (W): C O M P U T E R
Key (W): 1 4 3 5 8 7 2 6
A N O V I N C E
E W T A O T N Y
H E P R T U E M
A O I N Z Z T Z
Cipher: ANOVI NCEEW TAOTN YHEPR TUEMA OINZZ TZ
Example - Davies p26 Fig 2.15
Key(R): sorcery => 6 3 4 1 2 5 7 laser beams can be modulated to carry more intelligence than radio wavesgives
erasb lecam snabd umole atoed ctamo ryrre elntl iicee ntgha dnria oesav w
Example - Seberry p67-8 [3]
Seberry Table 3.1 p69
Key(R): s o r c e r y s o r c e r y
Key(R): 6 3 4 1 2 5 7 6 3 4 1 2 5 7
l a s e r b e l a s e r b e
a m s c a n b a m s c a n b
e m o d u l a e m o d u l a
t e d t o c a t e d t o c a
r r y m o r e r r y m o r e
i n t e l l i i n t e l l i
g e n c e t h g e n c e t h
a n r a d i o a n r a d i o
w a v e s w a v e s q r
Example - Sinkov p148
Sinkov p148
Example - Sinkov p 149-151
Plaintext: NOWISTHETIMEFORALLGOODMEN
Key (W): L E M O N
2 1 3 5 4
L 2 O N W S I
E 1 H T E I T
M 3 E M F R O
0 5 L A L O G
N 4 D O M N E
Nihilist Cipher: HTEIT ONWSI EMFRO DOMNE LALOG
Diagonal Cipher: ONHET WSEML DAFII TRLOM OOGNE
Example
- Davis Fig2.16 p27
Substitution Table
\\ A D F G V X A K Z W R 1 F D 9 B 6 C L 5 F Q 7 J P G X G E V Y 3 A N V 8 O D H 0 2 X U 4 I S T M
Plaintext: PRODUCTCIPHERS Intermediate Text: FG AG VD VF XA DG XV DG XF FG VG GA AG XG Keyed Block Columnlar Transposition Matrix
D E U T S C H Key 2 3 7 6 5 1 4 Sorted Order F G A G V D V F X A D G X V D G X F F G V G G A A G X G
Ciphertext: DXGX FFDG GXGG VVVG VGFG CDFA AAXA